Multi-tenant SaaS Architecture: Comparing Row, Schema, and Database Isolation
Multi-tenant applications are everywhere. Most modern SaaS projects handle multi-tenancy in different ways depending on their scale and security needs. In this post, I will share what I’ve learned about multi-tenancy architectures and how to choose the right one for your project.
What is a Multi-Tenant Application?
If you are building a B2B application with multiple clients (tenants), you need a way to separate their data while minimizing server costs. Instead of deploying a full stack for every new client, a well-designed multi-tenant app allows you to onboard new users with simple configuration changes, utilizing shared resources efficiently.
Database Implementation Strategies
While I will use PostgreSQL as an example, these concepts apply to most relational databases.
1. Server-Level Isolation
Each client gets their own dedicated database server (e.g., a separate AWS RDS instance).
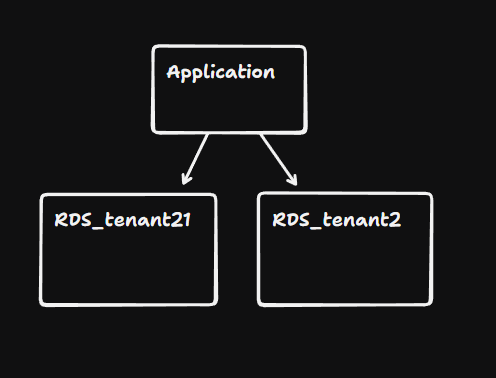
- Pros: Highest level of security and physical data isolation. No “noisy neighbor” effect.
- Cons: Extremely high maintenance and cost. Scaling to hundreds of clients is difficult.
- Best For: Government/Bank grade security
2. Database-Level Isolation
Multiple clients live on the same database server, but each has its own named Database.
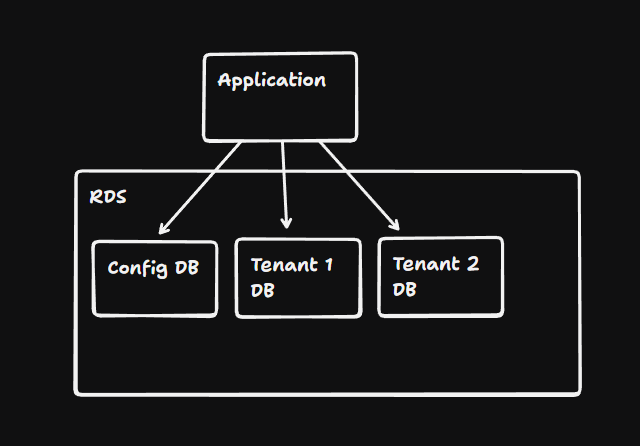
- Pros: Cheaper than server-level isolation; data is still physically separated into different files.
- Cons: Hard to manage connection pools; running migrations across 100+ databases is slow and risky.
- Best for: High-compliance industries like FinTech or Healthcare.
3.Schema Level
Using PostgreSQL Schemas. You have one “public” schema for global configs and separate schemas for each tenant. You can use the SET search_path TO tenant_name command to switch contexts.
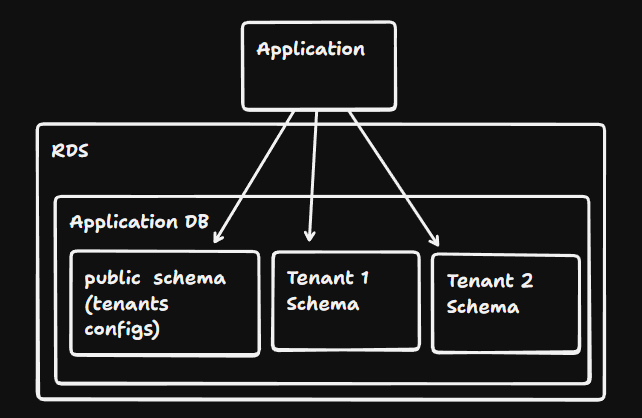
- Pros: Good balance of isolation and cost. Only one database connection pool is needed.
- Cons: Performance can degrade as the number of schemas reaches the thousands (due to system catalog bloat).
- Best For: High-value Enterprise clients
4.Table Level
Creating tables with prefixes like tenant1_users, tenant2_users.
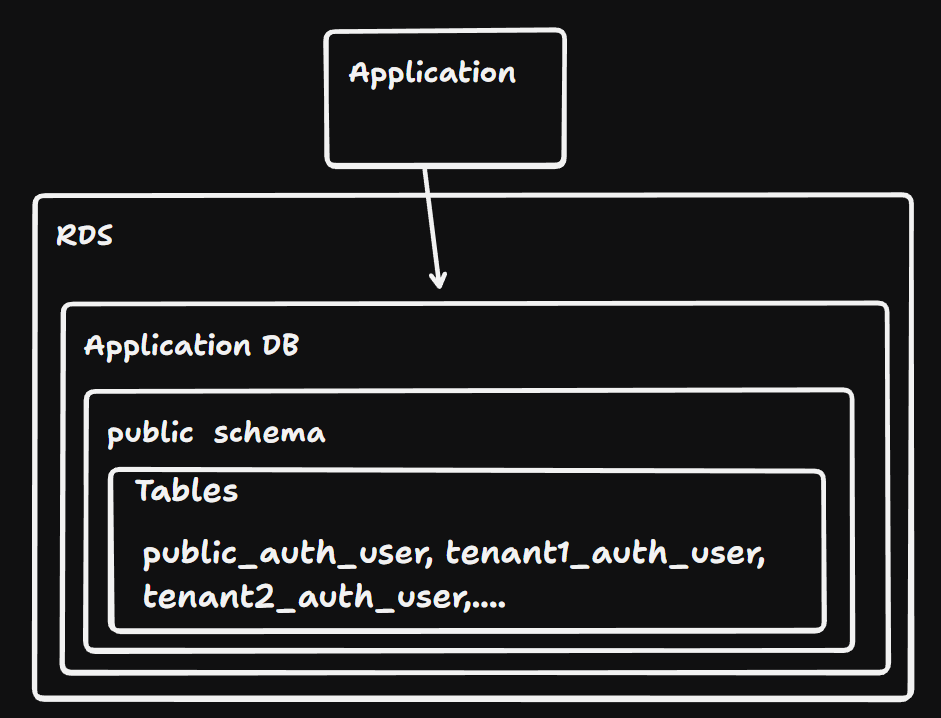
- Pros: Can offer some logical isolation.
- Cons: Not Recommended. It is a maintenance nightmare and most databases have limits on the number of tables per schema.
- Best For: Avoid this approach; it combines the weaknesses of all other methods. Don’t use this as my opinion
5. Row-Level Isolation
All tenants share the same tables. Every table includes a tenant_id foreign key. You use Row-Level Security (RLS) in Postgres to ensure one tenant cannot see another’s data.

- Pros: Highly scalable, lowest cost, and easiest to run migrations (you only run them once).
- Cons: High risk if the
tenant_idfilter is forgotten in a query (though RLS helps prevent this). Hard to perform a “backup and restore” for just one specific client. - Best For: Thousands of small-to-medium users and B2C applications
Below is comparison table for all
| Feature | Row Level (RLS) | Table Level (Prefixes) | Schema Level | Database Level | Server Level (RDS Instance) |
|---|---|---|---|---|---|
| Isolation | Logical (Policy) | Logical (Manual) | Logical (Namespace) | Physical (File/Process) | Physical (Hardware/Compute) |
| Maintenance | Easiest (1 table) | Hardest (1,000s tables) | Moderate | Hard (1,000s DBs) | Extreme (1,000s Instances) |
| Infrastructure Cost | Lowest | Medium | Medium | Highest (per DB) | Astronomical (Idle waste) |
| Server Management | Simple: One server to monitor & patch. | Complex: High metadata/memory load. | Moderate: Single server, but many objects. | Extreme: Managing thousands of DB instances/files. | Massive: Fleet-wide patching and orchestration. |
| Best For | High-growth SaaS | Not recommended | Balanced Enterprise | Banks / High Compliance | Ultra-Secure / Tier 1 Gov & Defense |
Application-Level Implementation
How do you tell your app which tenant is currently logged in?
- Middleware: The most common way. Intercept the request, identify the tenant, and set the database connection or
search_path. - Reverse Proxy: Using Nginx or specialized proxies to route requests to specific internal services based on the tenant.
- If you find any other ways please let me know also.
How to detect the Tenant from a request:
- Subdomains:
client-a.saas.com(Most professional/common). - Custom Headers: Passing a
X-Tenant-IDin the API header. - URL Path:
saas.com/tenant-a/dashboard. - JWT Claims: Encoding the
tenant_idinside the auth token (Very secure). There can be many other ways you can detect tenant from request.
That’s all for the blog if you have any feedback on the blog or want to ask something please mail at [email protected]